In Figure 13-8 the respective crypto map commands remain to compare two items. º Crypto map name.

Products Migration To Ipsec Virtual Tunnel Interface Cisco Ios Xe White Paper Cisco
3fd32rf09svc Perfect Forward Secrecy.
2 crypto map 1 interface. Step 2 crypto ipsec transform set transform set name transform1 transform2 from COMP NETWORKS at Memorial University of Newfoundland. Not Set Remote Gateway. One crypto map can be applied to an interface.
One crypto map can have multiple entries identified by a number. To accommodate multiple tunnels crypto map entries are used. Ip route 19216810 2552552550 1721612.
Group2 Hard Lifetime. Crypto map map2 interface outside. Ipsec-isakmp º Bind the crypto map CMAP to the outgoing interface.
Dyno and dyn1 at one crypto map outside_map with different sequence numbers the result - still at the. Md5 3des-cbc Encaps mode. MAIN IKE pre-shared key.
The thing is that I dont have any dynamic map created and Im not sure how to arrange the crypto maps to make it work. I know that its because there can be only one crypto map applied to an interface. CMAP º SA establishment.
28800 seconds 4608000 kilobytes Number of Transforms. The command show crypto session detail will show the state of the tunnel UP-ACTIVE and the pkts encrypteddecrypted. The Encryption method DES 3DES AES AES-192 or AES-256.
This is a big advantage over Crypto Maps. Crypto map sheepnet 19. Multiple IPSec Tunnels on Cisco routers interface.
I an trying to configure 2 IPSEC VPSN Tunnels on the Cisco 1941 WAN Port. Static crypto map can reference a dynamic crypto map. Crypto map map1 interface outside.
R1config int fa00 R1config-if crypto map CMAP R1config-if Oct 12 122015283. Same crypto map can be applied to multiple interfaces. GRE encapsulation allows having an interface Tunnel which can be used for dynamic routing.
The Authentication method either a pre shared key or an RSA signature is usual. R1configinterface fa00 R1config-ifcrypto map CRYPTOMAP. Lifetime In seconds before phase 1 should be re-established - usually 86400 seconds 1 day.
Crypto map RA_VPN_MAP interface outside 4. Below is main configs. There is only one crypto map per interface possible but the dynamic-map is used in an entry in the crypto-map so you need only one crypto-map to use dynamic and.
Crypto ipsec transform-set ranch esp-des esp-md5-hmac. Apply Crypto Map to the Public Interface. Use the command show crypto map to show the output of the configuration Proposal used peer IP address Transform Set used etc.
Thats all we have to do on R1. Similar configuration will be applied to ASA2. Ping the Lo1 interface 1722011 on R1 from PC-C.
ISAKMP IKE Mode. Interface serial 21 ip address 1721612 2552552550 crypto map to-central interface serial 32 ip address 10132 2552552550 crypto map to-remote ip route 1921681010 2552552550 10132. This simplifies the Proxy ACL that only.
Notice that the command crypto map is used both globally to create the map and locally on the interface. Verify that the Security Technology package license is enabled. Crypto ipsec security-association lifetime seconds 3600.
The Hashing Method MD5 or SHA. Enable crypto map for IKEv2 phase 2 on the outside interface. Crypto ikev2 enable outside client-services port 443 3.
Now you can apply the crypto-map to routers outside interface connected to ISP which is interface fastEthernet00 in our case. We will apply this crypto map to the ASA outside interface. ISAKMP is ON R1config-if.
So will I have two separate crypto maps applied to the same interface. The final step is to apply the crypto map to the outgoing interface of the. The two crypto map types discussed and their usage.
Enable crypto ikev2 for IKEv2 phase 1 on the outside interface. I would like it to failover automatically from one connection to. The Diffie Helman Group 1 2 or 5 usually.
Enable anyconnect on the outside interface of the Cisco ASA. Heres my existing crypto with names ips changed to protect the innocent. Repeat the site-to-site VPN configurations on R3 so that they mirror all configurations from R1.
The ipsec-isakmp tag tells the router that this crypto map is an IPsec crypto map. I would like to apply a crypto map to two interfaces in a Cisco ASA 5525-X. The two interfaces connect to two different ISPs.
ASA1config crypto map cmap 1 match address ACL1 ASA1config crypto map cmap 1 set peer 1010102 ASA1config crypto map cmap 1 set ikev2 ipsec-proposal P1 ASA1config crypto map cmap interface outside. Permit tcp host 1010212 neq 35 any Crypto map Type. The same that happens to Shaun.
The tunnel with the higher crypto map sequence pre-empts the lower sequence number so only one tunnel is active at a time. Now well create a similar configuration on R3. I need both to be active simultaneously.
Last but not least well activate the crypto map on the interface. Although there is only one peer declared in this crypto map 1112 it is possible to have multiple peers within a given crypto map. This is so that I have redundancy in the vpn tunnel which is ikev1 l2l vpn.
GRE over IPsec means that we do GRE first and encryption second. ASA2config crypto map cmap 1 match. Crypto map outside_map interface outside I attached two different crypto dynamic-map.
CCIE Routing Switching Written. You can apply only one crypto-map per interface.
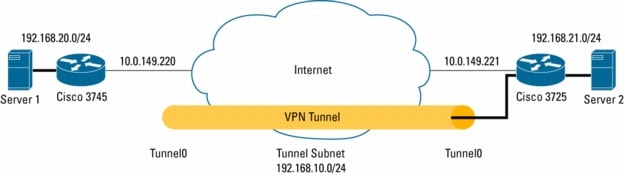
Configuring A Virtual Tunnel Interface With Ip Security Ipsec Negotiation Ike Protocols Cisco Systems
Ipsec Vpn Vs Ssl Vpn Vpn Sa Security
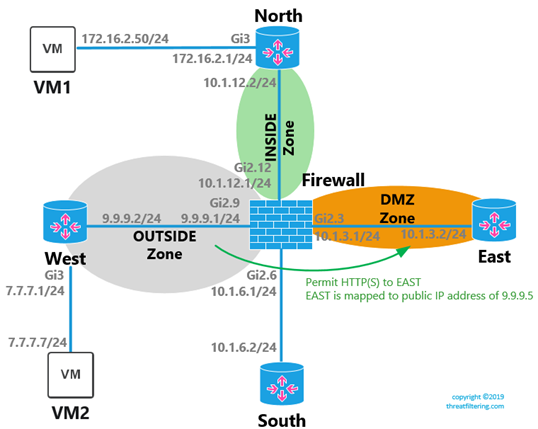
Cisco Zone Based Firewall Step By Step Part 2 Threat Filtering
Bridging Vpns Part 1 With Gns3 Lab Intense School

Step 5 Apply The Crypto Map To The Interface Iscw
Ikev2 L2l Vpn Using Crypto Maps Intense School
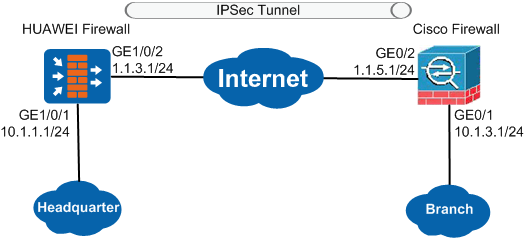
Establishing Ipsec Tunnels In Isakmp Mode Between Huawei Firewalls And Cisco Firewalls Huawei Usg Series Firewalls Interoperability Configuration Guide For Vpn Huawei
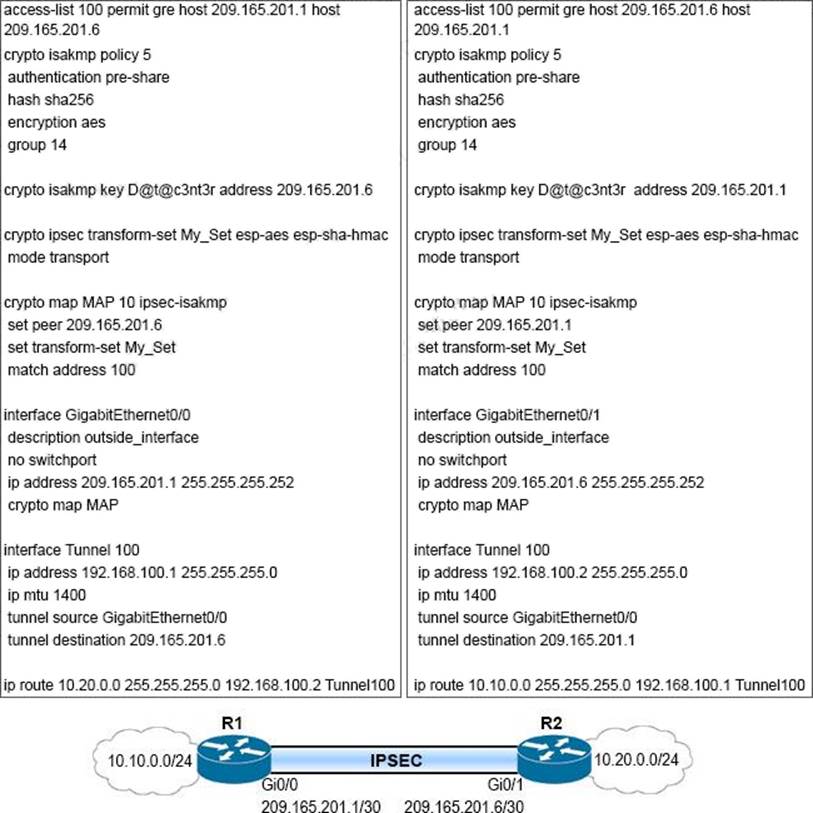
Which Two Configuration Changes Accomplish This Exam4training
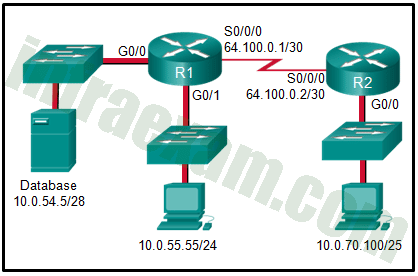
Refer To The Exhibit A Vpn Tunnel Is Configured On The Wan Between R1 And R2 On Which R1 Interface S Would A Crypto Map Be Applied In Order To Create A Vpn
What S Missing For My Ipsec Vpn

How To Configure Site To Site Ipsec Vpn Using Cisco Packet Tracer
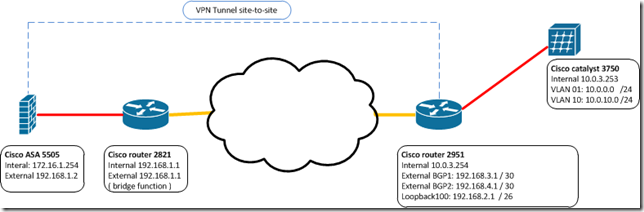
Fred De Jonge Cisco Router Site To Site Configuration On A Router With 2 Bgp Interfaces And 1 Loopback Interface With External Ip

Cli Book 3 Cisco Asa Series Vpn Cli Configuration Guide 9 12 Ipsec And Isakmp Cisco Asa 5500 X Series Firewalls Cisco

Ipsec Vpn Vs Ssl Vpn Vpn Sa Security
Site To Site Ipsec Vpn Between Palo Alto Networks Firewall And Knowledge Base Palo Alto Networks

Ipsec Crypto Map Vs Ipsec Tunnel Protection Demystified Demystify Much From Scratch

Ipsec Vpn Vs Ssl Vpn Vpn Sa Security

Route Based Vpn Between Cisco Router And Fortigate Firewall Using Ospf Ipsec Ssl Vpn
0 komentar